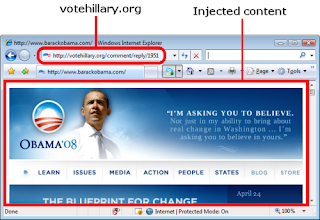
Following the recent cross-site scripting attacks against Obama (see previous post), Finnish security researcher Harry Sintonen has published an example of a cross-site scripting vulnerability on votehillary.org.
Sintonen's example submits a POST request to the Vote Hillary website and injects an iframe, causing the site to display the contents of Barack Obama's website. Unlike the Obama incident, which redirected the user's web browser, Sintonen's method retains the votehillary.org URL in the address bar while displaying the opposing website.
Sintonen told a Netcraft reporter that he was inspired by the recent Obama attacks and first examined Hillary Clinton's official website at www.hillaryclinton.com. Sintonen did not find any cross-site scripting vulnerabilities on this site, adding that it looked quite secure, but subsequently found XSS opportunities available on the Vote Hillary website. Sintonen lives in Finland and has no strong interest in US politics.
While the example exploits have so far been relatively benign (limited to redirecting a user to the opponent's website, for example), future cross-site scripting vulnerabilities found on political candidate sites have plenty of scope to be much more serious. Obama's and Clinton's websites both accept monetary contributions towards their campaigns, so cross-site scripting vulnerabilities could be leveraged to steal money and identities from supporters.
Sintonen told Netcraft he informed the webmasters of votehillary.org about this cross-site scripting vulnerability two days ago, but has not yet received a response.
No comments:
Post a Comment